Dissecting AQAP’s ‘Open-Source Jihad’: Understanding Its Digital Propaganda and Implications
Al-Qaeda in the Arabian Peninsula (AQAP), the Yemen-based affiliate of Al-Qaeda, has recently released a preview for an upcoming 46-minute video under the newly rebranded “Open Source Jihad” section of its “Inspire” label. The online English-language magazine Inspire [1]was first published in 2010 by al-Qaeda in the Arabian Peninsula to support this strategic shift to the strategy of “open-source jihad”.
The video, titled “What America & The West Do Not Expect,” calls for jihadist attacks in the United States, as a key ally of Israel and a direct contributor to the plight of the Ummah, Britain, France, and the European Union as retaliation for the Israel-Gaza conflict.
In addition to reinforcing their presence in the global discourse, the video is intended to resonate with their followers and potentially draw attention to their ongoing agenda and objectives. An integral aspect of this agenda is reflected in their publication “Inspire,” particularly through a segment named “Open Source Jihad.” In this section, would-be jihadists get detailed instructions on how to carry out independent terrorist attacks in Western countries. The rebranded OSJ may be something other than a magazine format. It could be a series of videos or an app.

The Content and the Narrative
AL Qaeda is canalizing the current wave of anti-West hatred due to the war between Israel and Gaza to mobilize terrorist attacks against the West

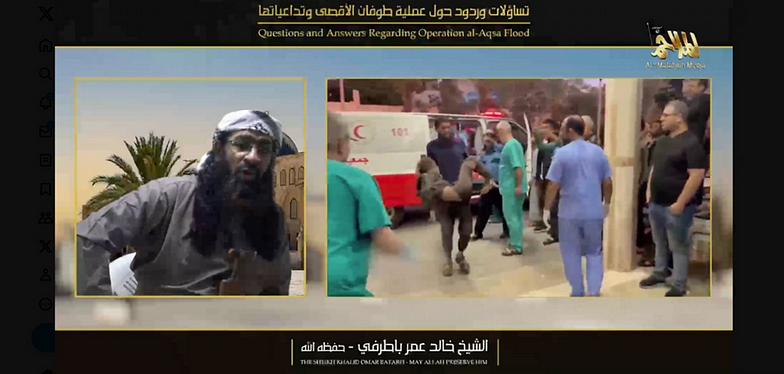






Victory Propaganda 2023
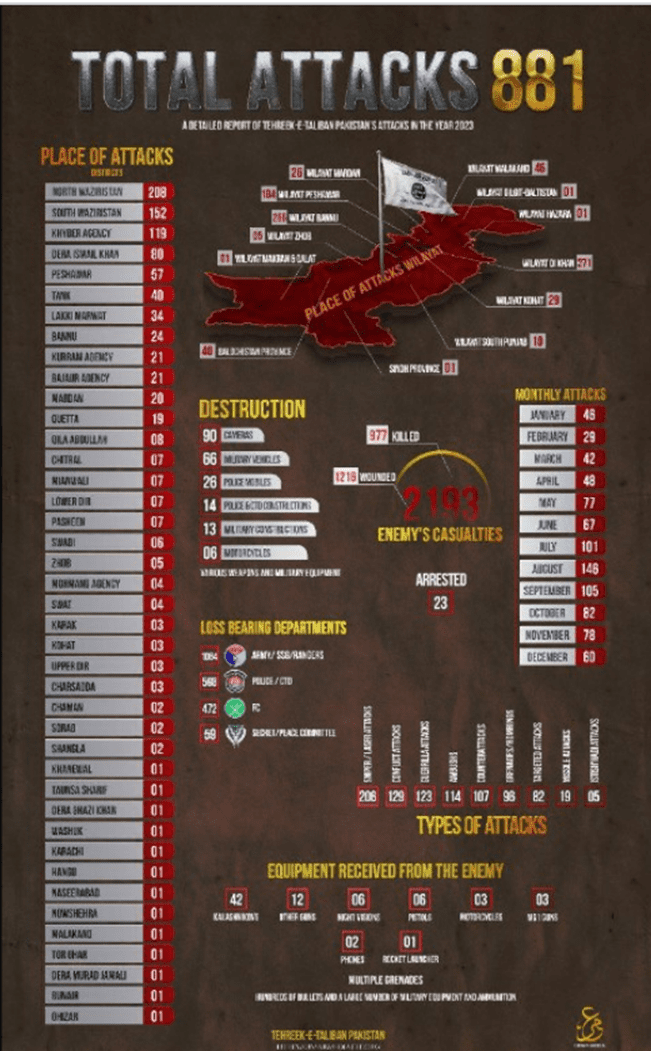
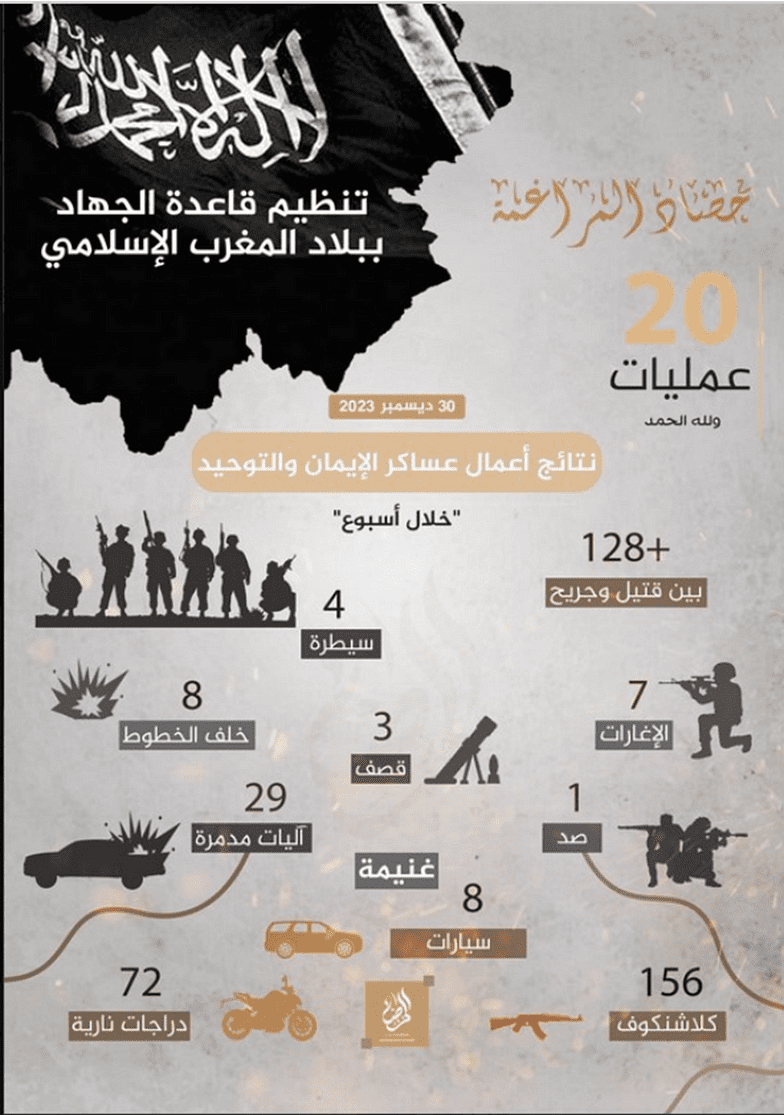
AL Qaeda affiliated groups in Pakistan and Maghreb also released two new posters in Chirpwire showing the number of attacks carried out by them through 2023.
Victory propaganda primarily serves to demonstrate a group’s strength and validate its actions, producing several key impacts:
- Morales Enhancement: Bolsters the spirits and loyalty of supporters and members, affirming the group’s cause and efficiency.
- Recruitment: Success stories can attract new members, influenced by the group’s apparent effectiveness.
- Psychological Impact: Aims to intimidate adversaries, creating an aura of invincibility around the group’s agenda.
- Legitimacy and Justification: Publicizes accomplishments to justify the group’s existence and actions, portraying itself as effective and legitimate.
- Perception Management: Shapes the narrative to focus on positive outcomes, influencing public opinion favourably.

Psychological Impact of Extremist Content
Having understood the nature of Al Qaeda’s propaganda, let’s explore its psychological ramifications on the targeted audience. Generally, because the stakes are so high, many who encounter such material are not influenced by it, at least not in the sense of accepting its challenge. It can, however, be seductive for those with an acute sense of victimhood. In turn, it seeks to replace shame associated with feelings of impotence or worthlessness with the experience of triumph. It exploits a fundamental feeling of humiliation by inserting an element of heroic resistance into it.
It is important to note that feelings of humiliation which may make a person vulnerable to propaganda of this type are not only feelings derived from a social or political reality, but they are also psychological in nature. The origin of these feelings may be found in the early stages of emotional development within a family, but, irrespective of where they originate, they represent a powerful internal process.
With the rising global reliance on the internet and the growing use of AI technology and immersive visual media, more people are looking to the digital realm for solutions to life’s difficulties. This trend heightens the likelihood that such appeals will resonate with their intended audience. Among these users, some will be grappling with intense internal humiliation and will be driven to find alleviation through active participation in the external world.
Exploiting Global Conflicts: The Escalation of Extremist Threats and the Challenge of Lone Wolf Attacks
Given the severity of the Hamas-Israel conflict, prospects for a resolution appear bleak. As with ISIS, Al Qaeda exploits the conflict to further its agenda. The extremists leverage the situation to encourage supporters to execute attacks in Western countries, to prompt indecisive individuals to take action, and to radicalize an expanding group of discontented people. It is expected that these efforts will significantly increase extremist violence in the West, which could result in fatalities.
Regardless of the actual number of individuals compelled to partake in acts of terror influenced by terrorists’ propaganda, the potential threat they pose can be significant.
Lone wolf attacks pose a challenge not because of the force of ground troops, but rather because they are a challenge of fighting ideology rather than a force of ground forces. As FBI Director Christopher Wray testified before Congress on October 31, 2023, “the range of threats…is enormous”[4].
However, before October 7, the United States was facing a broad range of terrorist threats [5]. While both al Qaeda and Islamic State are primarily involved in regional insurgencies, they still pose a threat to American citizens and establishments both internationally and within the U.S.[6]. The intensity of their operations in Africa[7], the Middle East[8], and Asia[9] increased in 2023[10]. Moreover, the developments in the Middle East are expected to deepen the existing political divisions within America.
Combating Extremism in the Digital Age: Strategies for Empowerment and Resilience
As we bid farewell to 2023, the emergence of Al Qaeda’s “Open Source Jihad” video underscores the enduring and complex challenge posed by extremist groups, both internationally and in the digital realm. In the face of such adversity, the resilience and adaptability of global terrorist movements render the mere suppression of online extremist content as challenging as trying to dam a stream with a fork.
To effectively mitigate the impact of such content, a multifaceted approach is essential. Foremost among these strategies is the empowerment of individuals, particularly the youth, through digital education and media literacy programs. These programs, centered on developing critical thinking skills and a nuanced understanding of online propaganda, play a vital role in fostering resilience against extremist narratives. Further, understanding the psychological appeal of extremist narratives is key to developing effective countermeasures. These groups often exploit feelings of alienation and injustice. In parallel, strengthening community bonds and cultivating a sense of belonging are key to diminishing the allure of extremist ideologies. Community engagement models, including digital community centers and gamification strategies, provide vital support, counselling, and education, acting as bulwarks against radicalization.
As digital platforms become the primary arena for extremist propaganda, the need for sophisticated content monitoring tools becomes imperative. AI-driven algorithms, with their ability to analyze vast amounts of data rapidly, are crucial in identifying and mitigating extremist content. The advent of cutting-edge technologies and community-driven initiatives offer new avenues for combating digital terrorism. AI and machine learning algorithms are increasingly being used for the automated detection of extremist content and the identification of potential radicalization pathways. Enhanced digital forensics, including deepfake detection and blockchain-based cryptocurrency tracking, are instrumental in disrupting the technological arsenal of extremists. Simultaneously, virtual and augmented reality technologies are being employed to create educational experiences that counter extremist narratives, fostering empathy and understanding, particularly in younger, vulnerable audiences.
On a broader scale, international cybersecurity initiatives and comprehensive policy frameworks for social media platforms are essential for a coordinated global response against digital terrorism. These strategies, complemented by blockchain technology for content verification and citizen reporting apps, empower the public to actively participate in counter-terrorism efforts.
In this endeavor, the collaboration of governments, non-profits, and community leaders is paramount. A united front, advocating for peace and tolerance, is crucial in addressing the threat posed by extremist ideologies. Through these concerted efforts, combining technological innovation with human-centric solutions, we can look forward to forging a more resilient and empowered society, capable of confronting the challenges of extremism in the digital age.

Policy Researcher and Strategist | Media Analyst
Sources:
- Inspire: Inside the al-Qaeda magazine: https://www.channel4.com/news/inside-the-al-qaeda-magazine
- Underpants ‘bomber’ was a DOUBLE AGENT who delivered device to CIA… and then pinpointed location of mastermind for fatal drone attack: https://www.dailymail.co.uk/news/article-2141573/Underwear-bomber-CIA-double-agent-located-al-Qaeda-mastermind-Yemen-drone-attack.html
- Securing Global Trade Routes: The Role of Operation Prosperity Guardian and International Responses in the Red Sea: https://igsda.org/securing-global-trade-routes-the-role-of-operation-prosperity-guardian-and-international-responses-in-the-red-sea/
- Director Wray’s Opening Statement to the Senate Committee on Homeland Security and Governmental Affairs: https://www.fbi.gov/news/speeches/director-wrays-opening-statement-to-the-senate-committee-on-homeland-security-and-governmental-affairs
- Counter Terrorism Guide, Historic Timeline: https://www.dni.gov/nctc/timeline.html#2010
- US Department of State, Policy Issues: Countering Terrorism: https://www.state.gov/policy-issues/countering-terrorism/
- Counter Terrorism Guide, Foreign Terrorist Organizations: https://www.dni.gov/nctc/ftos/isis_west_africa_fto.html
- Counter Terrorism Guide, Islamic State of Iraq and the Levant: https://www.dni.gov/nctc/groups/isil.html
- Counter Terrorism Guide, ISIS-PHILIPPINES: https://www.dni.gov/nctc/ftos/isis_philippines_fto.html
- Office of the Director of National Intelligence ; Annual Threat Assessment February 2023 https://www.dni.gov/files/ODNI/documents/assessments/ATA-2023-Unclassified-Report.pdf